Cloud Security, Simplified. Protect AWS, Azure, and GCP in Minutes
✔ Automate security audits
✔ Fix misconfigurations
✔ Affordable for SMBs & MSPs
Trusted & Integrated









Why Security Teams Choose NEXUSIAM
Automated Security Insights
Identify IAM, storage, and network misconfigurations instantly.
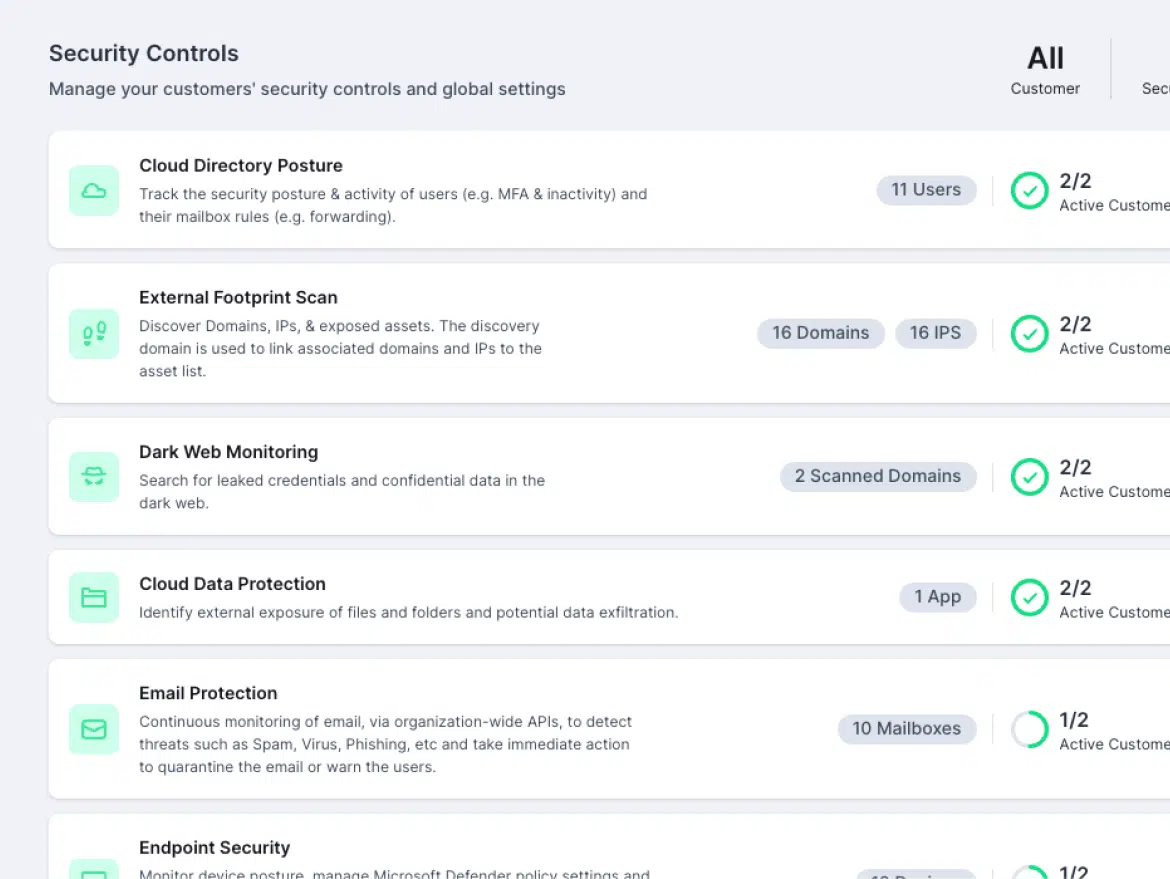
Multi-Cloud Security in One Dashboard
10x More Affordable Than Enterprise CSPMs
🔹 75% of cloud security failures are due to misconfigurations
🔹 NEXUSIAM scans & identifies security risks in under 15 minutes
NEXUSIAM Features
Multi-Cloud Security Monitoring
See all AWS, Azure, and GCP risks in one dashboard.
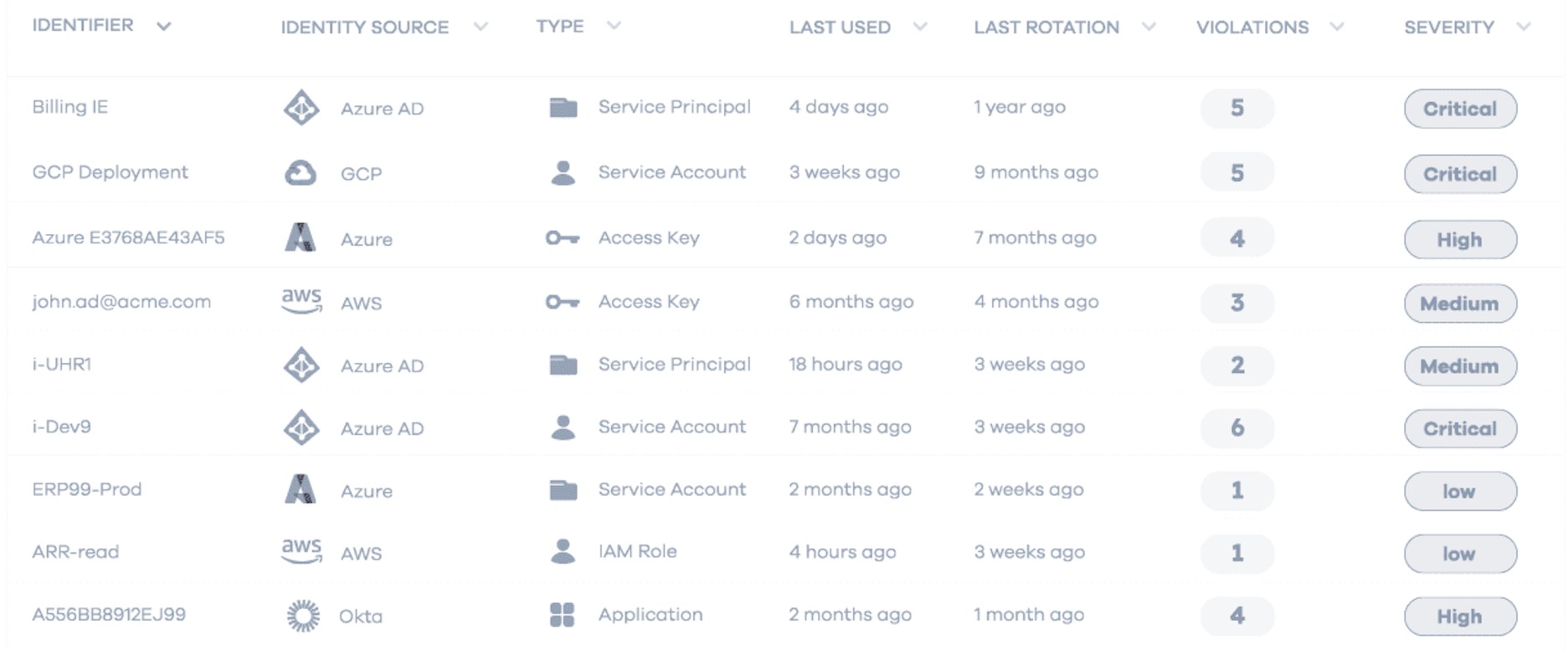
IAM & Permissions Scanning
Automated Fixes with GitOps
Terraform PRs automatically generated for security issues.
Instant Security Reports
Generate AWS Well-Architected & compliance reports in one click.
About us
At NEXUSIAM, we believe cloud security should be simple, effective, and affordable

🔹 Why We Exist
✔ Cloud security is broken. Most tools are expensive, noisy, and difficult to use.
✔ MSPs & SMBs don’t have enterprise security budgets. Prisma Cloud & Wiz are too costly for small teams.
✔ Security should be proactive, not reactive. Instead of waiting for breaches, we automate fixes.

🔹 Who We Serve
✔ Managed Service Providers (MSPs): Want automated security audits & reporting.
✔ SMBs & Startups: Need simple, cost-effective cloud security without hiring a security team.
Services
To help MSPs, MSSPs, and SMBs automate cloud security audits & remediation without enterprise pricing
1.
Cloud Security Posture Management (CSPM)
Multi-Cloud Security for AWS, Azure, and GCP
Security Risk Assessments
Automated Compliance Audits
AWS Well-Architected, CIS, NIST, and more.
Continuous Security Monitoring
2.
IAM & Permissions Security
Protect your cloud identities from unauthorized access
Detect & Fix Overprivileged IAM Roles
(AWS, Azure AD, GCP IAM).
Enforce Least Privilege Access
Automate Automatically.
Prevent IAM Drift & Policy Violations
Give reports in Real Time.
3.
Automated Security Remediation
GitOps-Based Security Fixes
Secure Storage & Network Configurations
Prevent Data Leaks & Breaches Before They Happen
4.
MSSP & MSP Partner Program
Multi-Tenant Cloud Security
Custom Branding & White-Label Reporting
Exclusive MSSP Partner Pricing
Contact NEXUSIAM
All Rights Reserved | Copyrights © 2025 NEXUSIAM.COM